Predefined alerts for log management
A predefined or default alert is a preconfigured AppLog search query-based notification that is automatically generated when a supported log type is created. By default, the alert is configured with one day (24-hours) frequency for a threshold value greater than or equal to zero (≥0). An alert is triggered as soon as the configured query violates the threshold within the specified time frame.
Default alerts of supported log types
The following are three alert types you can enable and customize:
- Trend Based Alert: Sends an alert when there is an unusual spike or drop over the configured days.
- Count Based Alert: Sends an alert when the number of log entries violates the threshold.
- New Data Detection Alert: Sends an alert when a new log entry has not appeared within a specific timeline.
The following is the list of supported log types:
ActiveMQ logs
Here is a predefined alert configured for ActiveMQ logs:
| Alert type | Alert name | Alert query |
|---|---|---|
| New Data Detection Alert | New Error Logs Contain Traceback or Exceptions | logtype="ActiveMQ Logs" and (message CONTAINS "traceback" or message CONTAINS "exception") groupby sourcefilename |
Akamai logs
Here are the predefined alerts that can be configured for Akamai logs:
| Alert type | Alert name | Alert query |
|---|---|---|
| New Data Detection Alert | New 4xx Failure Requests Detected | logtype="Akamai Logs" and statuscode>=400 and statuscode<500 groupby url |
| New 5xx Failure Requests Detected | logtype="Akamai Logs" and statuscode>=500 and statuscode<600 groupby url |
Apache Access logs
Here are the predefined alerts that can be configured for Apache Access logs:
| Alert type | Alert name | Alert query |
|---|---|---|
| Count Based Alert | Apache Slow Requests | logtype="Apache Access Logs" and status<400 groupby requesturi limit 100 |
| Apache Access Logs 500 Errors | logtype="Apache Access Logs" and status=500 | |
| Apache Access Logs 404 Errors | logtype="Apache Access Logs" and status=404 | |
| New Data Detection Alert | New 4xx Failure Requests Detected | logtype="Apache Access Logs" and status>=400 and status<500 groupby requesturi |
| New 5xx Failure Requests Detected | logtype="Apache Access Logs" and status>=500 and status<600 groupby requesturi | |
| New Requests Detected with Significant Data Sent in Response | logtype="Apache Access Logs" and responsesize>1000000 groupby requesturi | |
| Trend Based Alert | 500 Errors Trend | logtype="Apache Access Logs" and status=500 groupby requesturi |
| Time Taken Trend | logtype="Apache Access Logs"avg(timetaken) groupby requesturi |
Auth0 logs
Here are the predefined alerts configured for Auth0 logs:
| Alert type | Alert name | Alert query |
|---|---|---|
| Count Based Alert | Blocked IP | logtype="Auth0" and type="limit_mu" |
| Blocked Account | logtype="Auth0" and (type="limit_wc" or type="limit_sul") | |
| Breached password | logtype="Auth0" and type="pwd_leak" |
AWS API Gateway logs
Here are the predefined alerts configured for AWS API Gateway logs:
| Alert type | Alert name | Alert query |
|---|---|---|
| Count Based Alert | Slow Requests | logtype="AWS API Gateway Logs" and status<400 groupby resourcepath limit 100 |
| Internal Server Error | logtype="AWS API Gateway Logs" and status=500 | |
| Request URI Not Found | logtype="AWS API Gateway Logs" and status=404 | |
| New Data Detection Alert | New 4xx Failure Requests Detected | logtype="AWS API Gateway Logs" and status>=400 and status<500 groupby resourcepath |
| New 5xx Failure Requests Detected | logtype="AWS API Gateway Logs" and status>=500 and status<600 groupby resourcepath |
Caddy Access logs
Here are the predefined alerts configured for Caddy Access logs:
| Alert type | Alert name | Alert query |
|---|---|---|
| Count Based Alert | Slow Requests | logtype="Caddy Access Logs" and status<400 groupby uri limit 100 |
| Internal Server Error | logtype="Caddy Access Logs" and status=500 | |
| Request URI Not Found | logtype="Caddy Access Logs" and status=404 | |
| New Data Detection Alert | New 4xx Failure Requests Detected | logtype="Caddy Access Logs" and status>=400 and status<500 groupby uri |
| New 5xx Failure Requests Detected | logtype="Caddy Access Logs" and status>=500 and status<600 groupby uri | |
| New Requests Detected with Significant Latency | logtype="Caddy Access Logs" and latency>1000 groupby uri | |
| Trend Based Alert | 500 Errors Trend | logtype="Caddy Access Logs" and status=500 groupby uri |
Caddy Error logs
Here are the predefined alerts configured for Caddy Error logs:
| Alert type | Alert name | Alert query |
|---|---|---|
| New Data Detection Alert | New Error Logs Contain Traceback or Exceptions | logtype="Caddy Error Logs" and (message CONTAINS "traceback" or message CONTAINS "exception") groupby path |
| New 4xx Failure Requests Detected | logtype="Caddy Error Logs" and status>=400 and status<500 groupby path | |
| New 5xx Failure Requests Detected | logtype="Caddy Error Logs" and status>=500 and status<600 groupby path |
Cerberus FTP logs
Here are the predefined alerts configured for Cerberus FTP logs:
| Alert type | Alert name | Alert query |
|---|---|---|
| Count Based Alert | File Transfer Failed | logtype="Cerberus FTP Logs" and message contains "File transfer failed" |
| New Data Detection Alert | New Error Logs Contain Traceback or Exceptions | logtype="Cerberus FTP Logs" and (message CONTAINS "traceback" or message CONTAINS "exception") groupby clientip |
Cloud Front logs
Here are the predefined alerts that can be configured for Cloud Front logs:
| Alert type | Alert name | Alert query |
|---|---|---|
| New Data Detection Alert | New 4xx Failure Requests Detected | logtype="Cloud Front Log" and statuscode>=400 and statuscode<500 groupby stemuri |
| New 5xx Failure Requests Detected | logtype="Cloud Front Log" and statuscode>=500 and statuscode<600 groupby stemuri | |
| New Requests Detected with More TimeTaken | logtype="Cloud Front Log" and timetaken>1000 groupby stemuri | |
| Trend Based Alert | 500 Errors Trend | logtype="Cloud Front Log" and statuscode=500 groupby stemuri |
| Time Taken Trend | logtype="Cloud Front Log"avg(timetaken) groupby stemuri |
CodeIgniter logs
Here is a predefined alert configured for CodeIgniter logs:
| Alert type | Alert name | Alert query |
|---|---|---|
| New Data Detection Alert | New Error Logs Contain Exceptions | logtype="CodeIgniter Logs" and message contains "exception" |
Django logs
Here is a predefined alert configured for Django logs:
| Alert type | Alert name | Alert query |
|---|---|---|
| New Data Detection Alert | New Error Logs Contain Traceback or Exceptions | logtype="Django Logs" and (message CONTAINS "traceback" or message CONTAINS "exception") groupby module |
ELB Application logs
Here are the predefined alerts that can be configured for ELB Application logs:
| Alert type | Alert name | Alert query |
|---|---|---|
| New Data Detection Alert | New 4xx Failure Requests Detected | logtype="ELB Application Log" and elbstatuscode>=400 and elbstatuscode<500 groupby request |
| New 5xx Failure Requests Detected | logtype="ELB Application Log" and elbstatuscode>=500 and elbstatuscode<600 groupby request | |
| New Requests Detected with Significant Data Sent in Response | logtype="ELB Application Log" and bytessent>1000000 groupby request |
ELB Classic logs
Here are the predefined alerts that can be configured for ELB Classic:
| Alert type | Alert name | Alert query |
|---|---|---|
| New Data Detection Alert | New Error Logs Contain Traceback or Exceptions | logtype="ELB Classic Log" and elbstatuscode>=400 and elbstatuscode<=500 groupby request |
| New Requests Detected with Significant Data Sent in Response | logtype="ELB Classic Log" and bytessent>1000000 groupby request |
ELB Network logs
Here is a predefined alert configured for ELB Network logs:
| Alert type | Alert name | Alert query |
|---|---|---|
| New Data Detection Alert | New Requests Detected with Significant Data Sent in Response | logtype="ELB Network Log" and bytessent>1000000 groupby clienthost |
Fail2Ban logs
Here is a predefined alert configured for Fail2Ban logs:
| Alert type | Alert name | Alert query |
|---|---|---|
| Count Based Alert | Top Banned IPs | logtype="Fail2Ban Logs" and actiontaken="Ban" groupby machineip |
Fastly logs
Here are the predefined alerts that can be configured for Fastly logs:
| Alert type | Alert name | Alert query |
|---|---|---|
| New Data Detection Alert | New 4xx Failure Requests Detected | logtype="Fastly Logs" and statuscode>=400 and statuscode<500 groupby url |
| New 5xx Failure Requests Detected | logtype="Fastly Logs" and statuscode>=500 and statuscode<600 groupby url | |
| New Requests Detected with Significant Data Sent in Response | logtype="Fastly Logs" and response_body_size>1000000 groupby url |
GCP Kubernetes Node logs
Here is a predefined alert configured for GCP Kubernetes Node logs:
| Alert type | Alert name | Alert query |
|---|---|---|
| New Data Detection Alert | New Nodes Contain Failure | logtype="GCP Kubernetes Node Log" and (message CONTAINS "delete" or message CONTAINS "killing") groupby resource_labels_node_name |
Gitlab Runner logs
Here are the predefined alerts that can be configured for Gitlab Runner logs:
| Alert type | Alert name | Alert query |
|---|---|---|
| New Data Detection Alert | New Deployments Contain Failure | logtype="Gitlab Runner Logs" and (deploymentstatus="failed") groupby projectname |
| New Builds Contain Failure | logtype="Gitlab Runner Logs" and (status="failed") groupby buildname |
Gunicorn logs
Here are the predefined alerts that can be configured for Gunicorn logs:
| Alert type | Alert name | Alert query |
|---|---|---|
| Count Based Alert | Gunicorn Access Logs 500 Errors | logtype="Gunicorn Logs" and status=500 |
| Gunicorn Access Logs 404 Errors | logtype="Gunicorn Logs" and status=404 | |
| New Data Detection Alert | New 4xx Failure Requests Detected | logtype="Gunicorn Logs" and status>=400 and status<500 groupby requesturi |
| New 5xx Failure Requests Detected | logtype="Gunicorn Logs" and status>=500 and status<600 groupby requesturi | |
| New Requests Detected with Significant Data Sent in Response | logtype="Gunicorn Logs" and bytessent>1000000 groupby requesturi | |
| New Error Logs Contain Traceback or Exceptions | logtype="Gunicorn Logs" and (message CONTAINS "traceback" or message CONTAINS "exception") groupby remoteaddress | |
| Trend Based Alert | 500 Errors Trend | logtype="Gunicorn Logs" and status=500 groupby requesturi |
HAProxy logs
Here are the predefined alerts that can be configured for HAProxy logs:
| Alert type | Alert name | Alert query |
|---|---|---|
| New Data Detection Alert | New 4xx Failure Requests Detected | logtype="HAProxy Logs" and status>=400 and status<500 groupby requesturi |
| New 5xx Failure Requests Detected | logtype="HAProxy Logs" and status>=500 and status<600 groupby requesturi | |
| New Requests Detected with More TimeTaken | logtype="HAProxy Logs" and timetaken>1000 groupby requesturi | |
| Trend Based Alert | 500 Errors Trend | logtype="HAProxy Logs" and status=500 groupby requesturi |
| Time Taken Trend | logtype="HAProxy Logs"avg(timetaken) groupby requesturi |
Heroku logs
Here are the predefined alerts that can be configured for Heroku logs:
| Alert type | Alert name | Alert query |
|---|---|---|
| Count Based Alert | Slow Requests | logtype="Heroku Logs" and message_statuscode<400 groupby message_path limit 100 |
| Internal Server Error | logtype="Heroku Logs" and message_statuscode=500 | |
| Request URI Not Found | logtype="Heroku Logs" and message_statuscode=404 | |
| New Data Detection Alert | New Error Logs Contain Traceback or Exceptions | logtype="Heroku Logs" and message_statuscode>=400 and message_statuscode<=500 groupby message_path |
IIS Access logs
Here are the predefined alerts that can be configured for for IIS Access logs:
| Alert type | Alert name | Alert query |
|---|---|---|
| Count Based Alert | IIS Slow Requests | logtype="IIS Access Logs" and statuscode<400 avg(timetaken) groupby stemuri limit 100 |
| IIS Access Logs 500 Errors | logtype="IIS Access Logs" and statuscode=500 | |
| Time Taken Trend | logtype="IIS Access Logs" and statuscode=404 | |
| Trend Based Alert | 500 Errors Trend | logtype="IIS Access Logs" and statuscode=500 groupby stemuri |
| Time Taken Trend | logtype="IIS Access Logs"avg(timetaken) groupby stemuri | |
| New Data Detection Alert | New 4xx Failure Requests Detected | logtype="IIS Access Logs" and statuscode>=400 and statuscode<500 groupby stemuri |
| New 5xx Failure Requests Detected | logtype="IIS Access Logs" and statuscode>=500 and statuscode<600 groupby stemuri | |
| New Requests Detected with More TimeTaken | logtype="IIS Access Logs" and timetaken>1000 groupby stemuri |
IIS HTTP Error logs
Here are the predefined alerts that can be configured for IIS HTTP Error logs:
| Alert type | Alert name | Alert query |
|---|---|---|
| New Data Detection Alert | New 4xx Failure Requests Detected | logtype="IIS HTTP Error Logs" and statuscode>=400 and statuscode<500 groupby requesturi |
| New 5xx Failure Requests Detected | logtype="IIS HTTP Error Logs" and statuscode>=500 and statuscode<600 groupby requesturi | |
| Trend Based Alert | 500 Errors Trend | logtype="IIS HTTP Error Logs" and statuscode=500 groupby requesturi |
Java logs
Here is a predefined alert configured for Java logs:
| Alert type | Alert name | Alert query |
|---|---|---|
| New Data Detection Alert | New Error Logs Contain Traceback or Exceptions | logtype="Java Log" and (message CONTAINS "traceback" or message CONTAINS "exception") groupby classname |
Jenkins Application logs
Here is a predefined alert configured for Jenkins Application logs:
| Alert type | Alert name | Alert query |
|---|---|---|
| New Data Detection Alert | New Error Logs Contain Traceback or Exceptions | logtype="Jenkins Application Logs" and (message CONTAINS "traceback" or message CONTAINS "exception") groupby classname |
Kafka logs
Here is a predefined alert configured for Kafka logs:
| Alert type | Alert name | Alert query |
|---|---|---|
| New Data Detection Alert | New Error Logs Contain Traceback or Exceptions | logtype="Kafka Logs" and (message CONTAINS "traceback" or message CONTAINS "exception") groupby sourcefilename |
Kiwi Syslogs
Here is a predefined alert configured for Kiwi Syslogs:
| Alert type | Alert name | Alert query |
|---|---|---|
| New Data Detection Alert | New Error Logs Contain Traceback or Exceptions | logtype="Kiwi SysLogs" and (message CONTAINS "traceback" or message CONTAINS "exception") groupby host |
Kong API Gateway logs
Here are the predefined alerts that can be configured for Kong API Gateway logs:
| Alert type | Alert name | Alert query |
|---|---|---|
| Count Based Alert | Internal Server Error | logtype="Kong API Gateway Logs" and statuscode=500 |
| Request URI Not Found | logtype="Kong API Gateway Logs" and statuscode=404 |
Kubernetes Audit logs
Here are the predefined alerts that can be configured for Kubernetes Audit logs:
| Alert type | Alert name | Alert query |
|---|---|---|
| New Data Detection Alert | New 4xx Failure Requests Detected | logtype="Kubernetes Audit Logs" and responsestatus_code>=400 and responsestatus_code<500 groupby requesturi |
| New 5xx Failure Requests Detected | logtype="Kubernetes Audit Logs" and responsestatus_code>=500 and responsestatus_code<600 groupby requesturi |
Laravel logs
Here is a predefined alert configured for Laravel logs:
| Alert type | Alert name | Alert query |
|---|---|---|
| New Data Detection Alert | New Error Logs Contain Exceptions | logtype="Laravel Logs" and message contains "exception" |
Log4J logs
Here is a predefined alert configured for Log4J logs:
| Alert type | Alert name | Alert query |
|---|---|---|
| New Data Detection Alert | New Error Logs Contain Traceback or Exceptions | logtype="Log4J" and (message CONTAINS "traceback" or message CONTAINS "exception") groupby sourcefilename |
Log4Net logs
Here is a predefined alert configured for Log4Net logs:
| Alert type | Alert name | Alert query |
|---|---|---|
| New Data Detection Alert | New Error Logs Contain Traceback or Exceptions | logtype="Log4Net" and (message CONTAINS "traceback" or message CONTAINS "exception") groupby sourcefilename |
LogBack logs
Here is a predefined alert configured for LogBack logs:
| Alert type | Alert name | Alert query |
|---|---|---|
| New Data Detection Alert | New Error Logs Contain Traceback or Exceptions | logtype="LogBack" and (message CONTAINS "traceback" or message CONTAINS "exception") groupby sourcefilename |
Magento logs
Here is a predefined alert configured for Magento logs:
| Alert type | Alert name | Alert query |
|---|---|---|
| Count Based Alert | Security Problems | logtype="Magento Logs" and message contains "Security problem" |
Nginx logs
Here are the predefined alerts that can be configured for Nginx logs:
| Alert type | Alert name | Alert query |
|---|---|---|
| Count Based Alert | Nginx Access Logs 500 Errors | logtype="Nginx Logs" and status=500 |
| Nginx Access Logs 404 Errors | logtype="Nginx Logs" and status=404 | |
| New Data Detection Alert | New 4xx Failure Requests Detected | logtype="Nginx Logs" and status>=400 and status<500 groupby requesturi |
| New 5xx Failure Requests Detected | logtype="Nginx Logs" and status>=500 and status<600 groupby requesturi | |
| New Requests Detected with Significant Data Sent in Response | logtype="Nginx Logs" and bytessent>1000000 groupby requesturi | |
| Trend Based Alert | 500 Errors Trend | logtype="Nginx Logs" and status=500 groupby requesturi |
NLogs
Here is a predefined alert configured for Nlogs:
| Alert type | Alert name | Alert query |
|---|---|---|
| New Data Detection Alert | New Error Logs Contain Traceback or Exceptions | logtype="NLog" and (message CONTAINS "traceback" or message CONTAINS "exception") groupby sourcefilename |
OneLogin logs
Here are the predefined alerts that can be configured for OneLogin logs:
| Alert type | Alert name | Alert query |
|---|---|---|
| Count Based Alert | Login Failures | logtype="OneLogin Logs" and event_type_id in (6,9,77,154,901,905,906) groupby event_type_id |
| App User Limit Reached | logtype="OneLogin Logs" and event_type_id=20 count |
Opsgenie logs
Here are the predefined alerts that can be configured for Opsgenie logs:
| Alert type | Alert name | Alert query |
|---|---|---|
| Count Based Alert | Escalation Alert | logtype="Opsgenie Logs" and action="Escalate" |
| P1 Incident Alert | logtype="Opsgenie Logs" and priority="P1" |
PagerDuty logs
Here are the predefined alerts that can be configured for PagerDuty logs:
| Alert type | Alert name | Alert query |
|---|---|---|
| Count Based Alert | Escalation Alert | logtype="PagerDuty Logs" and eventtype="incident.escalated" |
| P1 Incident Alert | logtype="PagerDuty Logs" and priority="P1" |
PHP-FPM Slow logs
Here is a predefined alert configured for PHP-FPM Slow logs:
| Alert type | Alert name | Alert query |
|---|---|---|
| New Data Detection Alert | New Error Logs Contain Traceback or Exceptions | logtype="PHP-FPM Slow Logs" and (backtrace CONTAINS "traceback" or backtrace CONTAINS "exception" or backtrace CONTAINS "error") groupby scriptfilename |
PostgreSQL logs
Here is a predefined alert configured for PostgreSql logs:
| Alert type | Alert name | Alert query |
|---|---|---|
| New Data Detection Alert | New Error Logs Contain Traceback or Exceptions | logtype="PostgreSql Logs" and (message CONTAINS "traceback" or message CONTAINS "exception") groupby host |
Puppet Server Access logs
Here are the predefined alerts that can be configured for Puppet Server Access logs:
| Alert type | Alert name | Alert query |
|---|---|---|
| New Data Detection Alert | New 4xx Failure Requests Detected | logtype="Puppet Server Access Logs" and status>=400 and status<500 groupby requesturi |
| New 5xx Failure Requests Detected | logtype="Puppet Server Access Logs" and status>=500 and status<600 groupby requesturi | |
| New Requests Detected with More TimeTaken | logtype="Puppet Server Access Logs" and timetaken>1000 groupby remoteip | |
| Trend Based Alert | 500 Errors Trend | logtype="Puppet Server Access Logs" and status=500 groupby requesturi |
| Time Taken Trend | logtype="Puppet Server Access Logs"avg(timetaken) groupby requesturi |
RubyOnRails logs
Here is a predefined alert configured for RubyOnRails logs:
| Alert type | Alert name | Alert query |
|---|---|---|
| Count Based Alert | Exceptions | logtype="RubyOnRails" and message contains "exception" |
Squid Proxy logs
Here are the predefined alerts that can be configured for Squid Proxy logs:
| Alert type | Alert name | Alert query |
|---|---|---|
| Count Based Alert | IIS Slow Requests | logtype="Squid Proxy Logs"groupby url limit 100 |
| Requests Denied | logtype="Squid Proxy Logs" and code contains"DENIED" | |
| New Data Detection Alert | New 4xx Failure Requests Detected | logtype="Squid Proxy Logs" and status>=400 and status<500 groupby url |
| New 5xx Failure Requests Detected | logtype="Squid Proxy Logs" and status>=500 and status<600 groupby url | |
| New Requests Detected with Significant Data Sent in Response | logtype="Squid Proxy Logs" and bytessent>1000000 groupby url |
Syslogs
Here is a predefined alert configured for Syslogs:
| Alert type | Alert name | Alert query |
|---|---|---|
| Count Based Alert | Failed SSH Login | logtype="SysLog" and application="sshd" and (message CONTAINS "Failed" or message CONTAINS "Invalid user") |
Tomcat Access logs
Here are the predefined alerts that can be configured for Tomcat Access logs:
| Alert type | Alert name | Alert query |
|---|---|---|
| New Data Detection Alert | New 4xx Failure Requests Detected | logtype="Tomcat Access Logs" and status>=400 and status<500 groupby requesturi |
| New 5xx Failure Requests Detected | logtype="Tomcat Access Logs" and status>=500 and status<600 groupby requesturi | |
| New Requests Detected with Significant Data Sent in Response | logtype="Tomcat Access Logs" and bytessent>1000000 groupby requesturi | |
| Trend Based Alert | 500 Errors Trend | logtype="Tomcat Access Logs" and status=500 groupby requesturi |
Varnish logs
Here are the predefined alerts configured for Varnish logs:
| Alert type | Alert name | Alert query |
|---|---|---|
| Count Based Alert | Internal Server Error | logtype="Varnish Log" and status=500 |
| Request URI Not Found | logtype="Varnish Log" and status=404 | |
| New Data Detection Alert | New 4xx Failure Requests Detected | logtype="Varnish Log" and status>=400 and status<500 groupby requesturi |
| New 5xx Failure Requests Detected | logtype="Varnish Log" and status>=500 and status<600 groupby requesturi | |
| New Requests Detected with Significant Data Sent in Response | logtype="Varnish Log" and bytessent>1000000 groupby requesturi | |
| Trend Based Alert | 500 Errors Trend | logtype="Varnish Log" and status=500 groupby requesturi |
VPC Flow logs
Here is a predefined alert configured for VPC Flow logs:
| Alert type | Alert name | Alert query |
|---|---|---|
| New Data Detection Alert | New Requests Detected with Significant Data Sent in Response | logtype="VPC Flow Log" and bytes>1000000 groupby srcaddr |
WebLogic logs
Here are the predefined alerts that can be configured for WebLogic logs:
| Alert type | Alert name | Alert query |
|---|---|---|
| Count Based Alert | Internal Server Error | logtype="WebLogic Log" and status=500 |
| Request URI Not Found | logtype="WebLogic Log" and status=404 | |
| New Data Detection Alert | New 4xx Failure Requests Detected | logtype="WebLogic Log" and status>=400 and status<500 groupby url |
| New 5xx Failure Requests Detected | logtype="WebLogic Log" and status>=500 and status<600 groupby url | |
| New Requests Detected with Significant Data Sent in Response | logtype="WebLogic Log" and bytes>1000000 groupby url |
WebSphere logs
Here is a predefined alert configured for WebSphere logs:
| Alert type | Alert name | Alert query |
|---|---|---|
| New Data Detection Alert | New Error Logs Contain Traceback or Exceptions | logtype="WebSphere" (message CONTAINS "traceback" or message CONTAINS "exception") groupby classname |
Wildfly logs
Here is a predefined alert configured for Wildfly logs:
| Alert type | Alert name | Alert query |
|---|---|---|
| New Data Detection Alert | New Error Logs Contain Traceback or Exceptions | logtype="Wildfly Logs" and (message CONTAINS "traceback" or message CONTAINS "exception") groupby classname |
Windows Event logs
Here are the predefined alerts that can be configured for Windows Event logs:
| Alert type | Alert name | Alert query |
|---|---|---|
| Count Based Alert | Audit Logs Cleared | logtype="Windows Event Log" and level CONTAINS "Information" and message contains "The audit log was cleared" |
| Unsuccessful Login Attempts | logtype="Windows Event Log" and source CONTAINS "Microsoft-Windows-Security-Auditing" and (eventid=529 or eventid=4625) | |
| Audit Policy Changed | logtype="Windows Event Log" and source CONTAINS "Microsoft-Windows-Security-Auditing" and (eventid=612 or eventid=4719) | |
| Successful Password Resets | logtype="Windows Event Log" and source CONTAINS "Microsoft-Windows-Security-Auditing" and (eventid=628 or eventid=4724) | |
| System Resources Exhausted | logtype="Windows Event Log" and source CONTAINS "Microsoft-Windows-Security-Auditing" and (eventid=516 or eventid=4612) | |
| Account Database Change | logtype="Windows Event Log" and eventid=640 | |
| User Account Disabled | logtype="Windows Event Log" and source CONTAINS "Microsoft-Windows-Security-Auditing" and (eventid=629 or eventid=4725) | |
| Domain Policy Change | logtype="Windows Event Log" and source CONTAINS "Microsoft-Windows-Security-Auditing" and (eventid=643 or eventid=4739) | |
| Computer Account Deleted | logtype="Windows Event Log" and source CONTAINS "Microsoft-Windows-Security-Auditing" and (eventid=647 or eventid=4743) | |
| Count Based Alert | Insufficient Memory Available | logtype="Windows Event Log" and source CONTAINS "MSSQLSERVER" and eventid=17052 |
| Replacing System File Attempted | logtype="Windows Event Log" and eventid=64001 and source="Windows File Protection" | |
| Bad Disk Sector Detected | logtype="Windows Event Log" and eventid=7 and source="Disk" | |
| Application Uninstalled | logtype="Windows Event Log" and eventid=11724 and source="MsiInstaller" | |
| Chassis Intrusion Detected | logtype="Windows Event Log" and eventid=1 and source="OMCI" | |
| Unexpected Shutdown | logtype="Windows Event Log" and (eventid=6008 or eventid=41) |
Zoom Events logs
Here are the predefined alerts that can be configured for Zoom Events logs:
| Alert type | Alert name | Alert query |
|---|---|---|
| Count Based Alert | Meeting Issues | logtype="Zoom Events" and event="meeting.alert" |
| Webinars Issues | logtype="Zoom Events" and event="webinar.alert" | |
| Room Alerts | logtype="Zoom Events" and event="zoomroom.alert" |
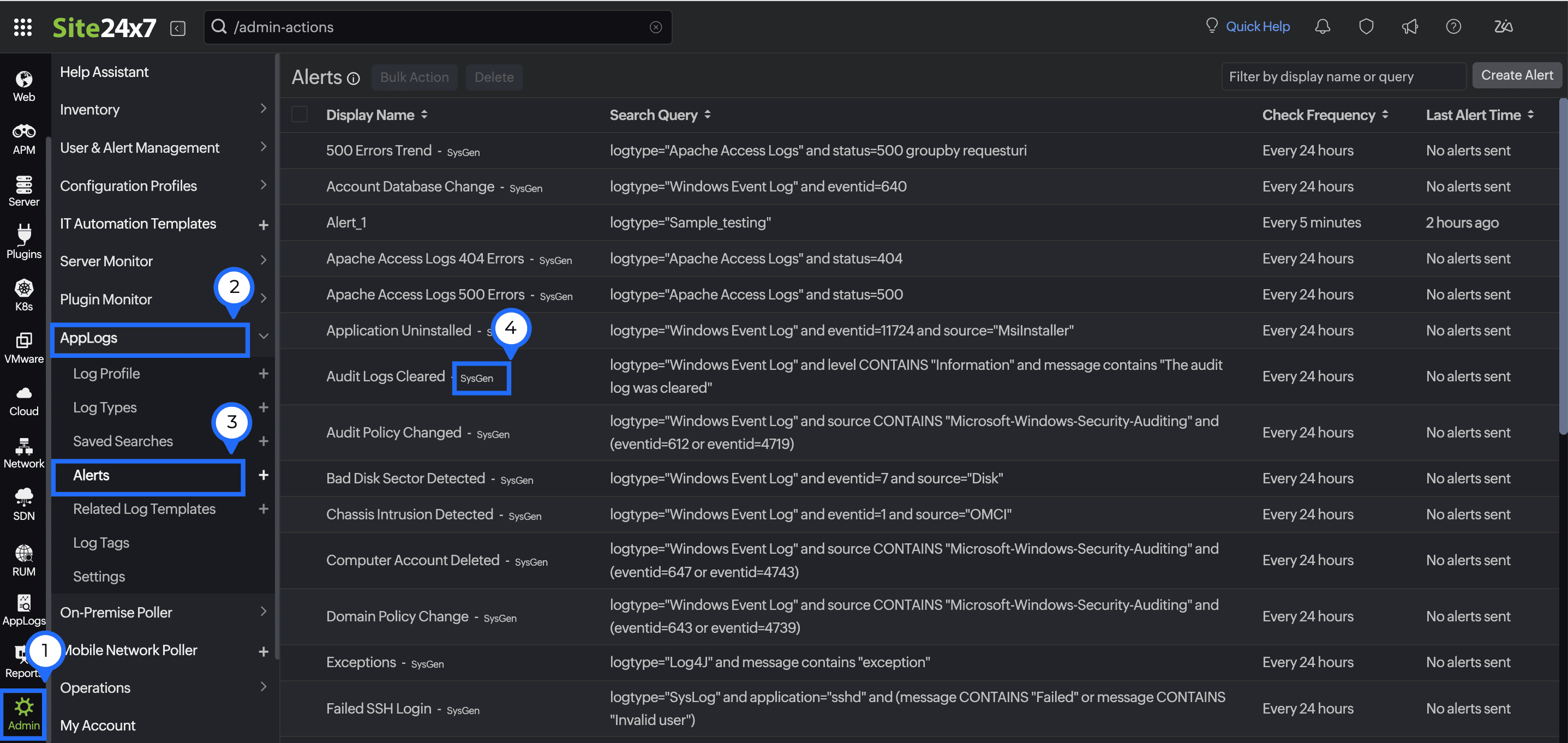
To view the saved alert settings:
- Go to Admin.
- Choose AppLog > Alerts.
- In the alert list, look for alerts tagged with "SysGen".The tag indicates alerts that are system generated.
Licensing
As these alerts are system-generated, they do not consume any license by default. However, if the check frequency is set to less than one day, these alerts will be subject to licensing, with each alert assigned a weightage of 0.1, which means they are priced as one basic monitor for 10 search queries. When a supported log type is created, Site24x7 auto-generates the corresponding predefined alerts and set up an AppLog monitor without using up the license.
Related articles
-
On this page
- Default alerts
- Licensing