What is a Kubernetes Resource Quota
A resource quota is a Kubernetes API object that limits aggregate resource consumption (compute, storage, number of objects, etc.) within a namespace. It's a mechanism for cluster administrators to ensure that a single team or application doesn't exhaust the shared cluster resources.
Key purposes:
- Prevent resource hogging by one namespace.
- Enforce fair usage among multiple tenants or teams.
- Control costs and ensure stability.
- Protect cluster control-plane and storage from overload (e.g. too many Secrets, too many pods).
How Resource Quota in Kubernetes works
- Enabling: The resource quota admission plugin must be enabled in the API server (most distributions have this on by default).
- Creation: An admin creates a Resource Quota object in a namespace, specifying specific hard limits on various resources.
- Usage tracking: Kubernetes keeps track of usage (status.used) of each resource in hard.
- Requests rejected: If creating a resource (Pod, PVC, etc.) causes usage to exceed the hard limit, that creation is rejected.
- Objects already existing are not automatically reduced or affected when quota limits change; quotas only prevent new requests that violate them.
Sample YAML: Resource Quota
Here's a basic example:
apiVersion: v1
kind: ResourceQuota
metadata:
name: compute-storage-quota
namespace: team-a
spec:
hard:
requests.cpu: "4" # total CPU requests in this namespace
requests.memory: "8Gi" # total memory requests
limits.cpu: "8"
limits.memory: "16Gi"
persistentvolumeclaims: "10" # number of PVCs
requests.storage: "100Gi" # total PV storage requested
pods: "20" # max pods in non-terminal state
With that:
- The resource quota restricts aggregate resource requests and limits for pods and PVCs created inside the team-a namespace.
- If any new pod or PVC creation request pushes these aggregate resources above the specified hard limits, the API server will reject the creation with an HTTP 403 error.
You can also use scopeSelector or scopes to restrict quotas to certain kinds of pods (by PriorityClass, etc.).
Practical use cases of Resource Quota
1. Multi-team shared clusters
In large organizations, multiple teams often share a Kubernetes cluster. Without quotas, one team deploying resource-heavy workloads can consume most of the cluster’s CPU or memory, starving others. By assigning each team its own namespace and resource quota, administrators can cap total compute, storage, and object usage per team. This ensures predictable performance, prevents noisy-neighbor issues, and enables accurate cost allocation per namespace.
2. Environment isolation (Dev/Test vs. Production)
Development and staging environments usually require fewer resources than production. Applying smaller quotas to dev or test namespaces prevents over-provisioning and helps maintain cost efficiency. It also provides a safety net against runaway deployments or CI/CD loops that could unintentionally overwhelm the cluster. Meanwhile, production namespaces can have relaxed quotas tuned to workload requirements, maintaining both agility and stability.
3. Priority-driven resource governance
ResourceQuota can be scoped using scopeSelector to enforce limits based on pod priority classes. This allows organizations to guarantee resource availability for critical services while containing less important or batch workloads. For instance, a high-priority quota can reserve CPU and memory exclusively for business-critical apps, ensuring they continue to run smoothly even under cluster pressure.
4. Control plane and storage protection
Quotas aren’t just for compute—they can cap the number of Kubernetes objects like Secrets, ConfigMaps, or PersistentVolumeClaims. This prevents unbounded object creation that could bloat etcd or overload the API server. Limiting these object counts is especially important in automated environments, where misconfigured jobs or operators could inadvertently flood the control plane with excessive metadata.
5. Compliance and cost management
In multi-tenant or regulated environments, quotas help enforce organizational policies such as per-team resource budgets or compliance with internal SLAs. They provide a measurable, auditable limit on resource usage that can be monitored via APIs or dashboards, making it easier to forecast costs and plan future capacity expansion.
Best practices
- Always define requests and limits for Pods to make quota enforcement effective.
- Combine Resource Quota with LimitRange to provide defaults (so users who forget specifying resources get sensible defaults).
- Restrict who can modify or delete Resource Quota objects (using RBAC, admission control) to avoid quota bypass or misconfiguration.
- Monitor usage (kubectl describe resourcequota) and set alerts when usage is close to limits.
- Use scopes to fine-tune quotas (priority, terminating vs non-terminating pods).
- Plan quotas considering cluster capacity (sum of quotas across namespaces should ideally not exceed cluster's actual resource capacity).
Things to watch out for
- Quotas do not affect existing resources when quota changes; only new resource creations are restricted.
- If a deployment is created that asks for more resources than quota allows, the deployment may still be accepted, but pods may remain in pending state. Users will need to debug.
- Resource Quota only tracks resources it is configured for; resources not specified are ignored.
- Ephemeral storage quotas and extended resource quotas might have behavior quirks (e.g. container logs count for ephemeral storage) which can lead to unexpected evictions.
- Scoping rules can be complex; mis-defining scopeSelector or overlapping quotas may lead to confusion.
Advanced features
- ScopeSelector/scopes: Allows matching only resources with certain attributes (priority class, best effort vs not, terminating etc.)
- VolumeAttributesClass: Newer feature to quota PVCs by their volume attribute classes.
- Cross-namespace Pod Affinity: Scopes can be used to limit pods with cross-namespace affinity terms.
Resource Quotas vs. limit ranges vs. requests
| Feature / Concern | ResourceQuota (Namespace) | LimitRange (Namespace policy) | Requests/Limits (Pod/Container) |
|---|---|---|---|
| Scope | Namespace aggregate | Per Pod/Container in namespace | Individual container spec |
| Primary purpose | Prevent overuse of cluster resources | Ensure defaults & per-object min/max | Define schedulable and enforceable container resources |
| Kinds controlled | CPU, memory, storage, object counts | CPU/memory only (per Pod/Container) | CPU/memory for that container |
| Tracking | Aggregates usage (status.used) | None, just constraints | No tracking, only per container runtime |
| Admission behavior | Rejects requests that exceed quota | Rejects or mutates invalid requests | Scheduler/Runtime enforcement |
| Change impact | Future creations blocked only | Future workloads enforced only | Defined once per spec |
| Best use case | “Team A gets max 10CPU” | “Pods must be between 100m–2CPU” | “Container needs 500m–1CPU” |
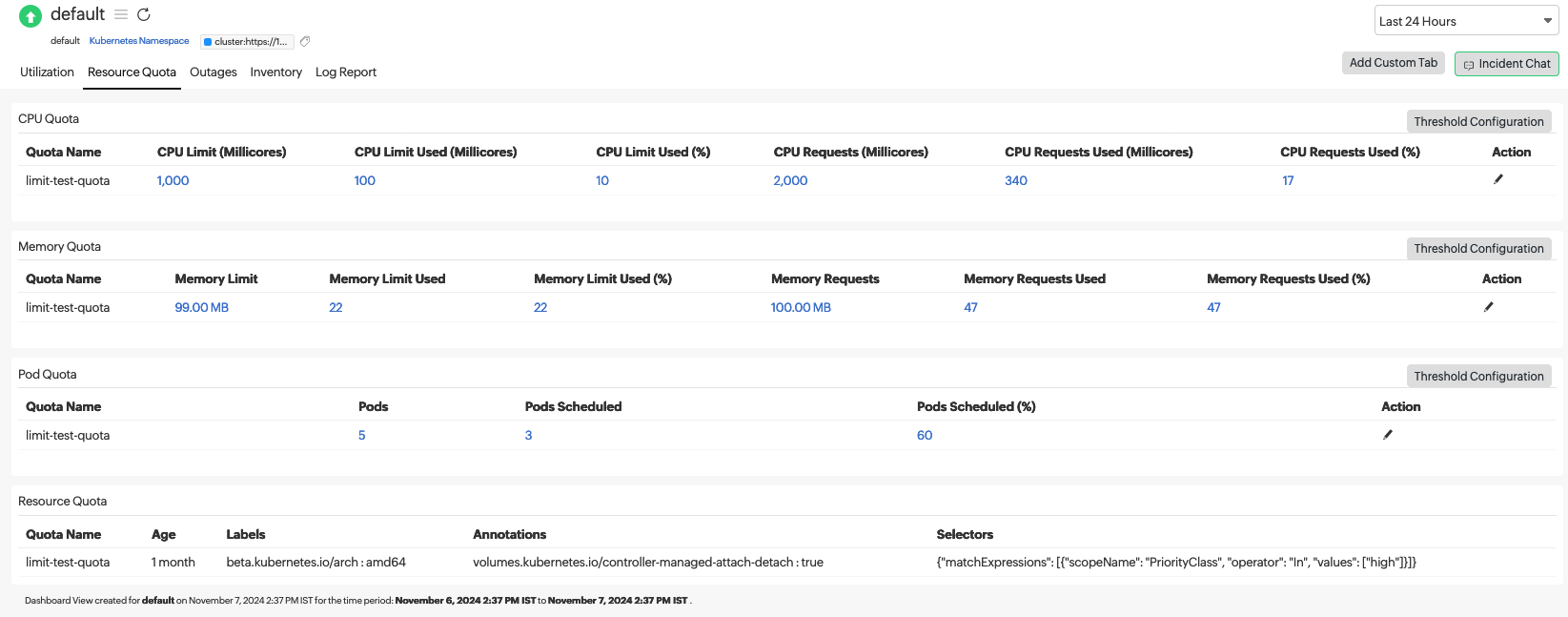
Simplify Resource Quota monitoring with Site24x7
Defining resource quotas is only the first step—observability and enforcement visibility are what make them truly effective. Site24x7 helps Kubernetes administrators go beyond static limits by offering real-time insights into quota usage, violations, and trends across all namespaces.
With Site24x7’s Kubernetes Resource Quota monitoring, you can:
- Visualize namespace-level quotas and usage for CPU, memory, storage, and object counts in a unified dashboard.
- Detect quota breaches instantly through intelligent alarms and anomaly detection.
- Correlate resource consumption with cluster performance and costs, ensuring teams stay within their allocated budgets.
- Automate alerting and capacity planning using AI-powered forecasting and usage analytics.
- Drill down into workloads to identify which pods or deployments are driving quota consumption.
Whether you’re managing multiple namespaces for different business units or maintaining a shared multi-tenant cluster, Site24x7 gives you end-to-end visibility—so you can enforce fairness, prevent overuse, and maintain cluster efficiency without manual tracking.
To wrap up
Resource Quota is a namespace-level policy that enforces limits on how much compute, storage, and object resources (like Pods, PVCs, or Secrets) can be created within that namespace. It helps ensure fair resource sharing, prevent any single team or workload from exhausting cluster capacity, and control costs. Quotas work by tracking usage against defined “hard” limits and rejecting new resources that would exceed them. They can be scoped to specific workloads (e.g., best-effort pods, priority classes) and are best used alongside LimitRanges, RBAC, and monitoring to maintain stability, efficiency, and governance in multi-tenant Kubernetes environments.